Office Access Control System
一、 System Introduction
ReconReCon has developed its Enterprise Access Control and Attendance System based on a philosophy of comprehensive R&D, security and simplicity. The Attendance system is a solution which meets the needs of large businesses.
ReCon’s Enterprise Access Control and Attendance System is based on facial recognition technology, and works via internet and 3G network communications, utilizing both centralized monitoring and a decentralized management model. This high-performing management model ensures the smooth implementation of company policy and performance appraisals, enhancing management efficiency and improving the company’s core competitiveness. Thanks to the wide applicability of the system, access and attendance control is possible on both local and wide area networks. The system allows for hierarchical management settings, so that recorded data is effectively protected and monitored. It is also simple to use, so that functions such as data queries, attendance management, staff scheduling, statistical calculations, report exporting and log queries can all be easily performed remotely.
二、System Functions
三、System Overview
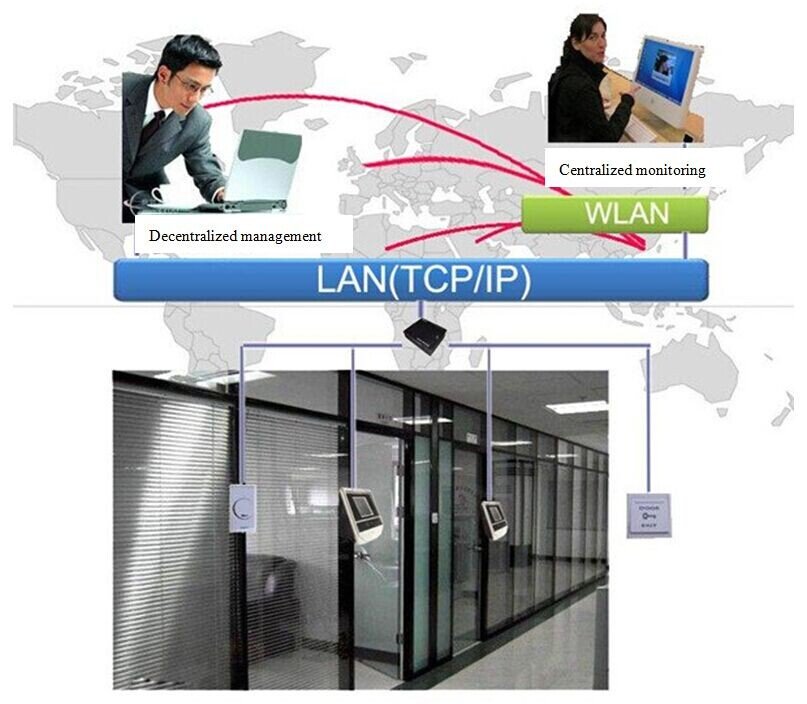
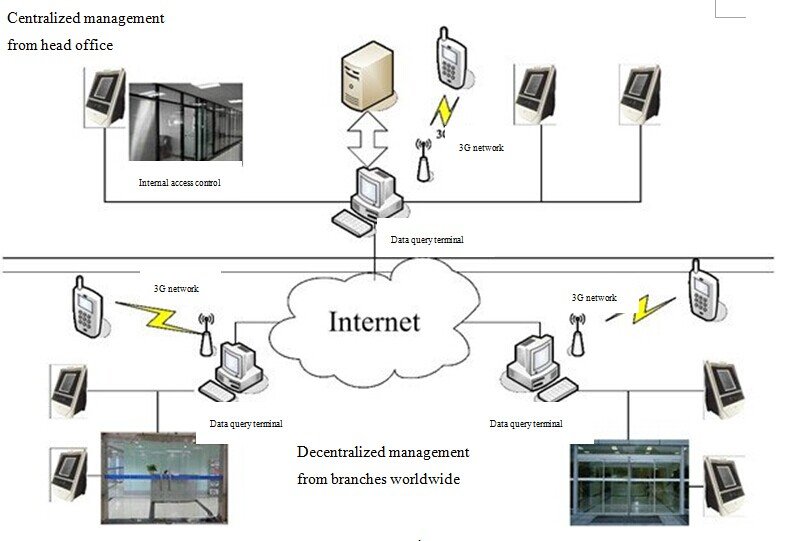
System operation schematic
 The global reach of the internet lays the foundation of ReCon’s Enterprise Access Control and Attendance System. Based on B/S network architecture, the system is characterized by completeness, security, and simplicity of use. Powerful features result in an access control system that is truly intelligent and secure.
The global reach of the internet lays the foundation of ReCon’s Enterprise Access Control and Attendance System. Based on B/S network architecture, the system is characterized by completeness, security, and simplicity of use. Powerful features result in an access control system that is truly intelligent and secure.
Once the identity and other information of a user is detected at a facial recognition terminal, the access control and attendance settings are triggered. Employee identification data (including the identification result and operation record) is transmitted over the internet for storage in the head office server. This information can be queried at any branch on a data terminal, or it may be accessed on a mobile device. Managers at head office can utilize data terminals to query the identification information of all employees in the company. The system is convenient to use: once enrolled, users can be identified on other face recognition terminals, so there is no need to repeat enrollment when in different geographical regions, and employees can utilize the system to apply for leave and overtime. Security and confidentiality are other key characteristics of the Enterprise Access Control and Attendance System. A hierarchical permissions scheme is used, with different permissions set for different regions, effectively controlling system entry and access to information and allowing fully confidential management of user information.
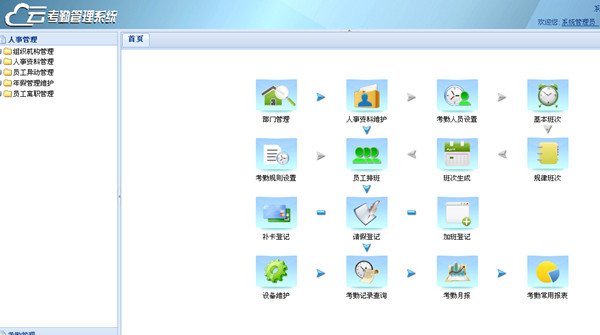
四、Attendance Management Platform
Screenshot of attendance platform
The system’s management platform runs on B/S (Browser/Server) architecture, a network architecture developed after the rise of the Internet, in which web browsers are the most important client software. Its advantage is that it can be operated from anywhere without having to install any special software – a computer with Internet access is all it takes. The attendance platform involves three key management modules: 1. Personnel management: this handles organizational structure management, personnel information management, employee transfer management, annual leave management and employee turnover management; 2. Attendance management: this module includes workforce management, attendance management, attendance machine data, leave management, overtime management, attendance data analysis, and monthly attendance report management; 3. System management: operating time settings, system enrollment information, system role management, and system user management.
五、Access Control System
The access control system consists of hardware devices (facial recognition terminals, access controllers, door bells, exit buttons, power locks, power sources etc.).
The diagram below shows the system workflow:
Access Control System Schematic
All access control stations are equipped with a facial recognition access control terminal, and access is based on facial recognition technology (supplemented by a card or password) to identify the user. Once recognition is successful, the system settings are triggered (such as opening or closing a door, using a printer, etc.), and all identified information is transmitted over the Internet to head office for storage. This information can then be viewed by managers with the right permissions.
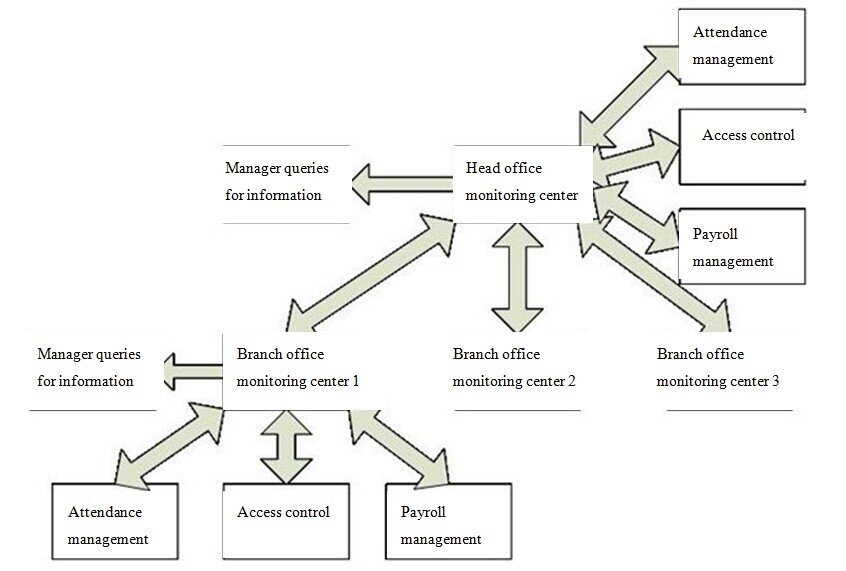
六、System Operation Flowchart
System flowchart
七、System Features:
● Network communication, wide coverage: managers can carry out monitoring remotely, and users can access the system at any terminal once obtaining permission.
● Set permissions for secure and confidential data: limits are imposed on the access of managers and users to safeguard user information.
● High precision, accuracy and reliability: the latest face recognition algorithms are used to ensure every face is accurately identified.
● High stability and low energy consumption: A high-performance, low-power DSP processor is used, operating completely off-line. The system has performed stably in long-term running tests, while automatic sleep mode is supported to conserve energy and protect the environment.
● Simple, user-friendly interface: A TFT LCD touch screen is complemented by a user-friendly GUI interface and web client management software.
● Versatile identification modes for enhanced security: Modes can be flexibly set according to user needs – examples include face recognition only, password + face, and ID/IC card + face recognition.
● Intelligent self-learning function: Human faces are automatically captured, and a self-learning function is incorporated. The face database is dynamically updated for changes in hairstyle, skin color, age, so that human faces are always correctly recognized.
● Real-time face logging: Real-time logging makes manual querying, identifying and verifying easier and more intuitive, as well as making it convenient to print and view.
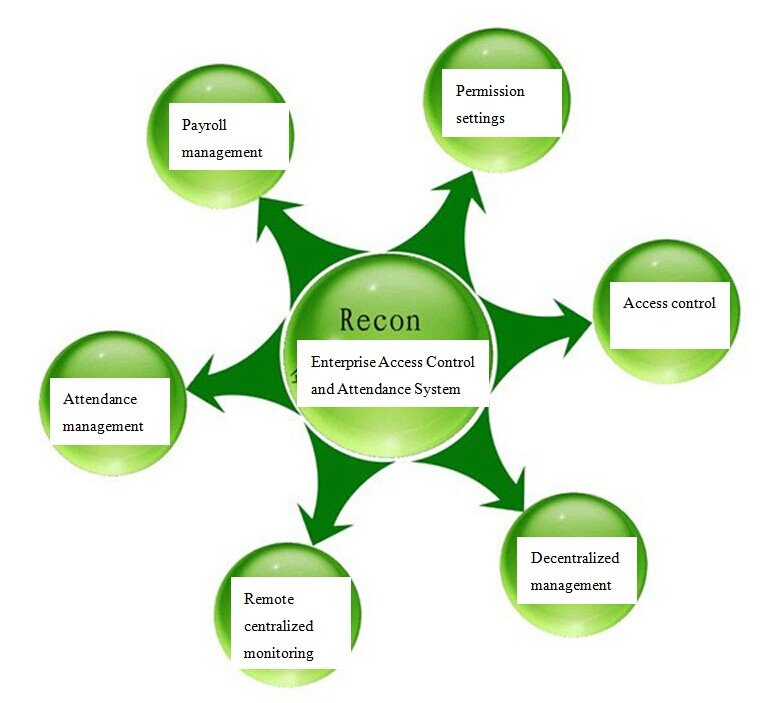
 The global reach of the internet lays the foundation of ReCon’s Enterprise Access Control and Attendance System. Based on B/S network architecture, the system is characterized by completeness, security, and simplicity of use. Powerful features result in an access control system that is truly intelligent and secure.
The global reach of the internet lays the foundation of ReCon’s Enterprise Access Control and Attendance System. Based on B/S network architecture, the system is characterized by completeness, security, and simplicity of use. Powerful features result in an access control system that is truly intelligent and secure.